How it works
Employees receive a direct message in Slack when they take high risk actions like making changes to infrastructure with an AWS key or running a large Terraform.
This message notifies employees about the potential risk of their behavior while gathering information for your security team about the employee's verification, intention, and sequence of actions.
Crowdalert automatically maps employee identities across accounts and systems so you can quickly see every action they took throughout your environment.
For high risk actions, you can also use Crowdalert to get round trip confirmation with out of band verification such as a WebAuthn click.
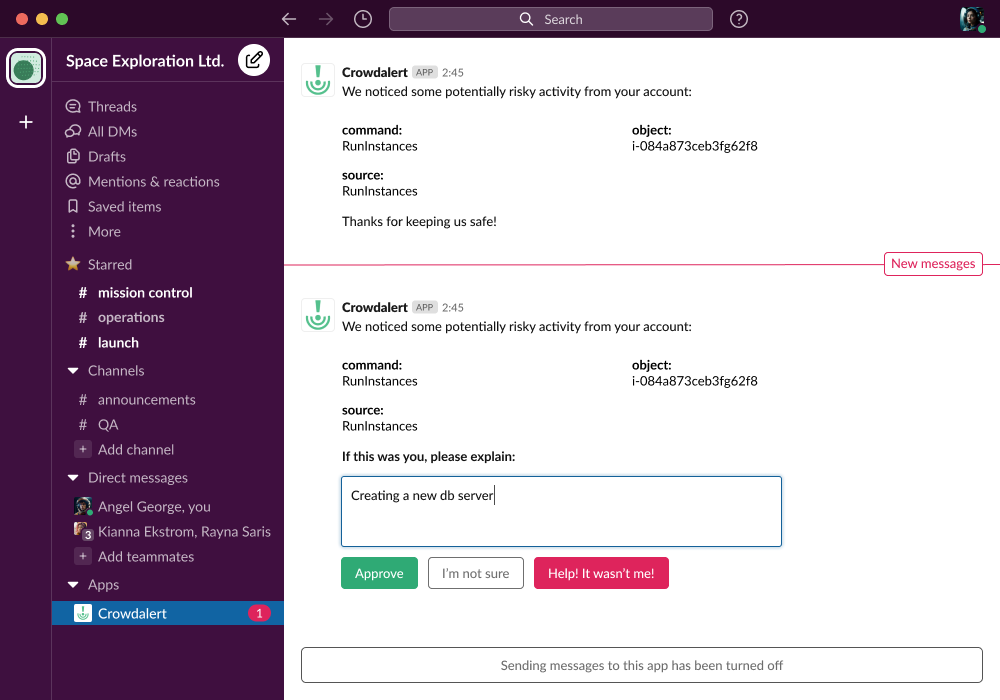
Reliable, precise, and thorough alerts mean better investigations.
Respond faster and more effectively to high-risk situations such as account takeovers (ATO), business email compromise (BEC), and privilege escalation attacks.
Improve security through trust instead of fear.
We built Crowdalert after seeing firsthand the benefits of trusted, two-way communication between employees and security teams. Crowdalert works like another member of your team automatically enriching and prioritizing alerts with out-of-band verification, attribution, and employee feedback.
Connect to any data source.
Crowdalert connects directly through the Datadog Vector pipeline for visbility across your systems.